PowerFolder <17.3 affected by Information Disclosure Vulnerability (CVE-2022-38793) #CampusCloud
Vendor of Product: dal33t GmbH
Affected Product Code Base: PowerFolder <17.3
Affected Component: list of share links (powerfold.er/linkstable)
Vulnerability Type: Incorrect Access Control
Impact: Information Disclosure
Attack Type: Remote
Attack Vectors: authenticated, logic flaw exploit
Has vendor confirmed or acknowledged the vulnerability? Yes
Reference: https://powerfolder.atlassian.net/wiki/spaces/PF/pages/2150072341/PowerFolder+Server+17+SP3
Suggested description: In dal33t PowerFolder before 17.3.102, an authenticated attacker can obtain a list of all file-share links of all users, even though the intended behavior is to obtain the list of only this user's own links.
To exploit this, the attacker must visit /linkstable before creating any folder of their own.
This vendor tracks this issue as "INT-642 - Link visibility problems when user has no folders."
Discoverer: the developers knew about the vulnerability and its severity but did not inform their customers (dozens of universities and some companies in Germany and abroad).
When I discovered the unpatched vulnerability in my University's CampusCloud and found out the customers haven't been informed by the vendor, I decided to request a CVE and make this publication.
Please, use this information responsibly and only to urge the admins of affected instances to update immediately. The exploit requires a verified personal account and PowerFolder logs any access to those share links.
You can also take a look at the login page's source code to check the version:
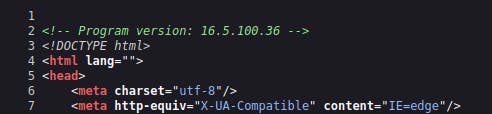
Every version <17.3 is vulnerable.
